What is Hashing ?
Hashing is a process of converting input data, such as a text, file, or any other piece of information, into a fixed-size string of characters, which is usually a hexadecimal or alphanumeric representation. Hash functions are mathematical algorithms that take an input and produce a hash digest, which is a fixed-size output. One of the important properties of hash functions is that they are designed to be irreversible, meaning it is computationally infeasible to reverse the process and obtain the original input from the hash digestTop of Form

What is SHA ?
The Secure Hash Algorithms (SHA) are a family of cryptographic hash functions that are published by the National Institute of Standards and Technology (NIST) in the United States. SHA is a widely used standard for producing fixed-size hash digests that are used for various cryptographic purposes, such as data integrity verification, digital signatures, and message authentication.
There are several members in the SHA family, including:
-
- SHA-1: It is a 160-bit hash function that was published in 1995. However, SHA-1 is now considered weak and insecure due to vulnerabilities found in its design, and it has been deprecated for most security applications.
- SHA-2: It is a family of hash functions that includes SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, and SHA-512/256. These hash functions are widely used and considered to be secure. They produce hash digests of different sizes, ranging from 224 bits to 512 bits, and are widely used in various cryptographic applications.
- SHA-3: It is the latest member of the SHA family, and it was published in 2015. SHA-3 is designed to provide improved security and resistance against different types of attacks compared to SHA-2. SHA-3 includes hash functions such as SHA3-224, SHA3-256, SHA3-384, SHA3-512, SHAKE128, and SHAKE256.
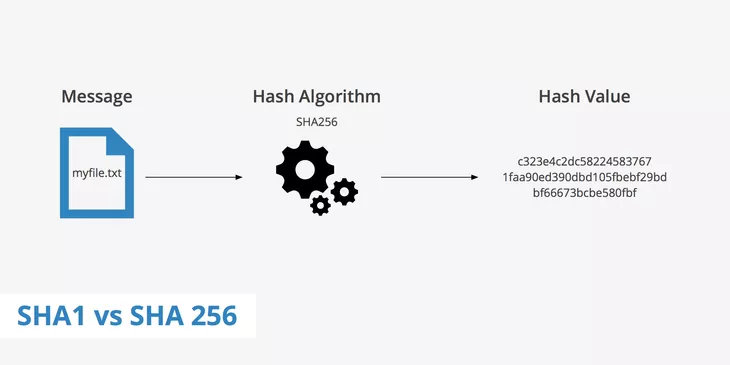
General characteristics of the Secure Hash Algorithms (SHA):
-
- One-way function: SHA is a one-way function, meaning it is designed to be irreversible. It is computationally infeasible to obtain the original input data from the hash digest. This property ensures that the original data cannot be easily reconstructed from the hash value, providing data security.
- Fixed-size output: SHA produces a fixed-size output, which is typically a string of characters in hexadecimal or alphanumeric format. The size of the output, or the hash digest, depends on the specific variant of SHA being used (e.g., SHA-1 produces a 160-bit hash digest, SHA-256 produces a 256-bit hash digest, etc.). The fixed-size output allows for efficient storage and comparison of hash values.
- Deterministic: SHA is deterministic, meaning that the same input data will always produce the same hash digest. This property ensures that hash values can be consistently generated and compared for data integrity verification and authentication purposes.
- Avalanche effect: SHA exhibits the avalanche effect, meaning that even a small change in the input data will result in a significantly different hash digest. This property ensures that even minor changes in the input data will produce vastly different hash values, providing a high level of data integrity verification.
- Cryptographic strength: SHA is designed to be cryptographically secure, meaning that it resists various types of attacks, such as pre-image attacks, second pre-image attacks, and collision attacks. This property ensures that it is computationally infeasible to reverse the hash function or find two different inputs that produce the same hash digest, providing data integrity and authenticity.
- Standardized: SHA is a widely recognized and standardized cryptographic hash function, with different variants published by NIST. This makes SHA suitable for interoperability and compatibility in various applications and systems.
The Secure Hash Algorithms (SHA) generally follow the same basic steps to generate a hash digest:
-
- Data Preparation: The input data is prepared for hashing. This typically involves converting the data into a standardized format, such as binary or UTF-8 encoding.
- Padding: The input data is padded to ensure that it meets the required block size of the specific SHA variant being used. Padding is necessary to ensure that the hash function operates on fixed-size blocks of data.
- Message Digest Initialization: An initial value, called the "message digest," is set for the hash function. The message digest serves as the starting point for the hash computation.
- Iterative Hashing: The input data, after being prepared and padded, is processed through multiple rounds of hashing. In each round, a chunk of data is processed along with the current message digest to produce an updated message digest. This process is repeated for all the chunks of data until the entire input data has been processed.
- Finalization: Once all the data has been processed, the final message digest is obtained. This typically involves performing additional operations on the last block of data and the current message digest to obtain the final hash digest.
- Output: The final hash digest is the resulting output of the SHA function. It is typically represented as a fixed-size string of characters in hexadecimal or alphanumeric format.
