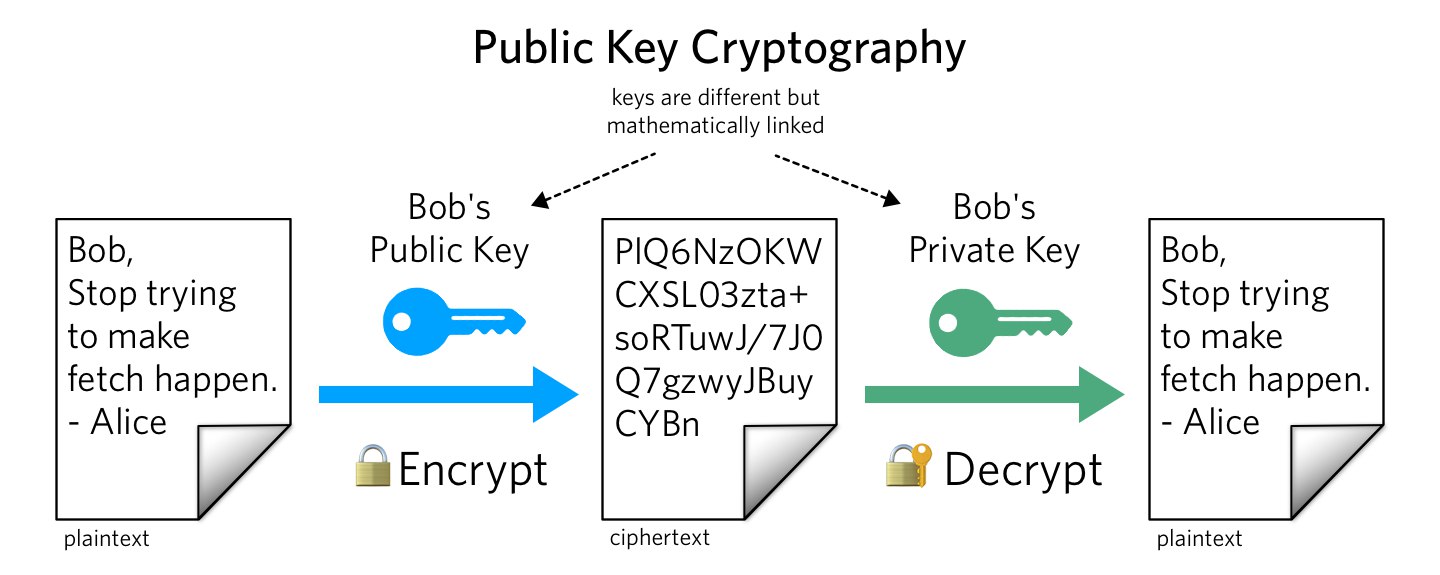
A public key is one of the two keys used in a public key cryptography system, which is a type of asymmetric cryptography. It is freely shared and used for encryption and verification. It is typically used to encrypt messages or data that are intended to be sent to the owner of the corresponding private key. It can also be used to verify digital signatures created with the private key, allowing for authentication and integrity verification
Here are some key reasons why public key cryptography is considered secure:
1. Key Pair:
Public key cryptography uses a pair of keys - a public key and a private key - that are mathematically related but computationally infeasible to derive from one another. The private key is kept secret by the owner, while the public key can be freely shared. This means that even if someone has the public key, they cannot easily determine the corresponding private key, which is required for decryption.
2. Encryption and Decryption:
Public key cryptography uses different keys for encryption and decryption. Data encrypted with the public key can only be decrypted with the corresponding private key, and vice versa. This ensures that only the intended recipient, who possesses the private key, can decrypt the encrypted data.
3. Computational Complexity:
The encryption algorithms used in public key cryptography are designed to be computationally complex, making it difficult for unauthorized entities to decrypt encrypted data by trying all possible keys through brute-force attacks
4. Secure Key Exchange:
Public key cryptography also allows for secure key exchange protocols, such as Diffie-Hellman, which enable two parties to establish a shared secret key over an insecure communication channel without exchanging the actual secret key.
5. Digital Signatures:
Public key cryptography also enables the use of digital signatures, which provide a way to verify the integrity and authenticity of data. A digital signature is created using the private key and can be verified using the corresponding public key.
Transferring cryptocurrencies using keys typically involves the following steps:
1. Wallet Creation:
The sender and the recipient each need to have a digital wallet, which is a software program or hardware device that stores their cryptocurrency keys. The wallet generates and manages the keys required for sending and receiving cryptocurrencies.
2. Public Key Sharing:
The sender needs to obtain the recipient's public key, which is typically a string of characters that serves as the recipient's cryptocurrency address. The recipient can share their public key with the sender through various means, such as through a QR code, a text message, an email, or any other agreed-upon method.
3. Transaction Creation:
The sender initiates a transaction by creating a digital transaction message that includes the recipient's public key, the amount of cryptocurrency to be transferred, and any transaction fees required by the cryptocurrency network. The transaction is usually created and signed using the sender's private key, which is kept secure in their wallet.
4. Transaction Broadcasting:
The signed transaction is then broadcasted to the cryptocurrency network, typically through the internet, to be verified and confirmed by the network of cryptocurrency nodes. The transaction is propagated through the network and eventually included in a block of transactions.
5. Transaction Confirmation:
The transaction needs to be confirmed by the cryptocurrency network through a process called mining or validation, depending on the specific cryptocurrency protocol. Miners or validators verify the transaction's validity, ensure that the sender has sufficient funds, and confirm that the transaction meets the cryptocurrency's rules and consensus mechanisms. Once the transaction is confirmed, it is considered as completed.
6. Transaction Receipt:
Once the transaction is confirmed, a transaction receipt is generated, which serves as proof of the transaction. The receipt typically includes transaction details, such as the transaction ID, timestamp, sender's and recipient's addresses, amount transferred, and other relevant information. The receipt may be stored in the sender's and recipient's wallets for future reference.
