A private key is a crucial component of a public key cryptography system. It is a secret, randomly generated key that is paired with a public key. The private key is kept securely by the owner and should not be shared with anyone else. It is used for decrypting messages or data that have been encrypted with the corresponding public key, as well as for creating digital signatures to authenticate and verify the integrity of data.
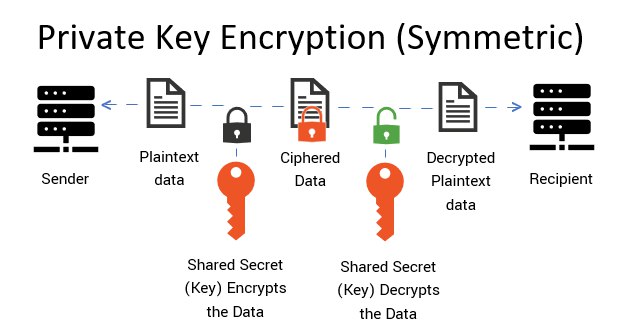
Here are some key reasons why private key cryptography is considered secure:
1. Strong Encryption:
Private key cryptography uses strong encryption algorithms that are computationally infeasible to reverse without the private key. This makes it extremely difficult for unauthorized parties to decrypt messages or data encrypted with the private key, ensuring confidentiality.
2. Asymmetric Nature:
Private key cryptography uses a pair of keys, namely a public key and a private key, that are mathematically related but computationally infeasible to derive from one another. This asymmetric nature of the keys adds an extra layer of security, as the private key is kept secret and not shared, while the public key can be freely shared for encryption or verification.
3. Secrecy of Private Key:
The private key, which is required for decrypting messages and creating digital signatures, is kept secret by the owner and not shared with others. This ensures that only the owner can access the encrypted data or generate valid digital signatures, preventing unauthorized access or tampering of data.
4. Authentication:
Private key cryptography allows for authentication, as digital signatures created with the private key can verify the integrity and authenticity of data. This helps in establishing the identity of the sender and ensuring the integrity of data, which is crucial in secure communication and transactions.
5. Scalability:
Private key cryptography allows for secure communication between multiple parties without the need for a shared secret key. This makes it scalable for use in various scenarios, such as secure communication over the internet, secure financial transactions, and secure access to online accounts.
6. Widely Used and Vetted Algorithms:
Private key cryptography is based on well-established and widely used encryption algorithms, such as RSA, DSA, and ECC, which have been extensively vetted and analyzed by the cryptographic community. This adds to the confidence in the security of private key cryptography.
7. Secure Key Management:
Private key cryptography requires careful management of the private key to ensure its secrecy and integrity. With proper key management practices, such as storing the private key in a secure location, using strong passphrase or hardware security modules (HSMs) for protection, and regular key rotation, the private key can be kept secure and prevent unauthorized access.
The process of generating and using keys in cryptography typically involves the following steps:
1. Key Generation:
In a public key cryptography system, a key pair consisting of a public key and a private key is generated. The public key is intended to be shared with others, while the private key must be kept secret by the owner. The key pair is mathematically related, but it is computationally infeasible to derive the private key from the public key, ensuring the security of the system.
2. Encryption:
To encrypt a message or data using public key cryptography, the sender uses the recipient's public key to perform the encryption process. This typically involves applying a mathematical algorithm to the plaintext data along with the recipient's public key, producing ciphertext that is unintelligible without the corresponding private key.
3. Decryption:
To decrypt the ciphertext and retrieve the original plaintext data, the recipient uses their private key to perform the decryption process. This typically involves applying a mathematical algorithm to the ciphertext along with the recipient's private key, producing the original plaintext data.
4. Digital Signatures:
In addition to encryption and decryption, public key cryptography can also be used for digital signatures. A digital signature is created by applying a mathematical algorithm to a piece of data using the private key, producing a unique signature Key Exchange: Public key cryptography also enables secure key exchange protocols, such as Diffie-Hellman, which allow two parties to establish a shared secret key over an insecure communication channel without exchanging the actual secret key. This helps prevent eavesdropping or man-in-the-middle attacks, which could compromise the security of the communication.
5. Key Management:
Key management is a critical aspect of cryptography. It involves generating, storing, distributing, and revoking keys securely to ensure their confidentiality, integrity, and availability. Proper key management practices, such as using strong random number generators, protecting private keys with strong passwords, and regularly updating and rotating keys, are important for maintaining the security of the cryptographic system.
